In our data-driven age, it’s difficult to overstate the importance of cyber security. Ransomware, cyberattacks, file corruption, and other unexpected events can undermine the integrity and resiliency of critical data stores and spell disaster for an organization. Protecting vital data is so essential that it’s too risky to rely on passive strategies and outdated technologies. A smarter approach is to combine the strength of proactive data protection strategies with state-of-the-art backup and management appliances.
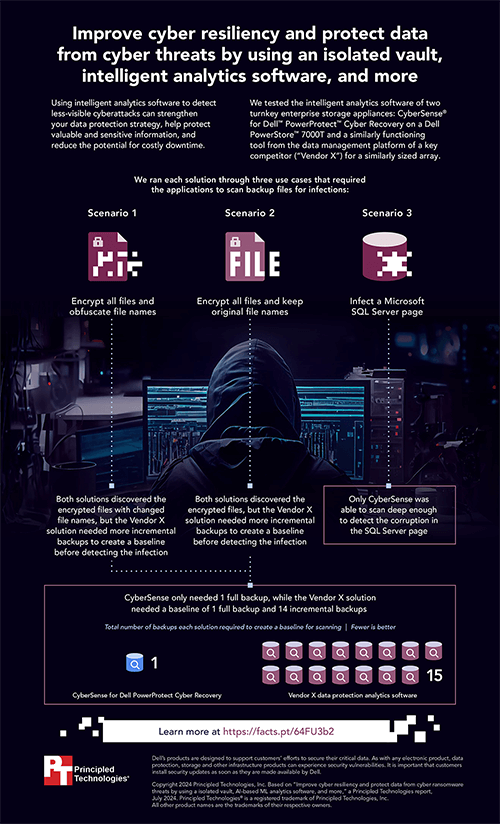
We conducted database protection tests on two turnkey enterprise data protection and cyber recovery solutions that utilized AI-based intelligent analytics software. The first solution consisted of CyberSense for Dell PowerProtect Cyber Recovery on a Dell PowerStore 7000T appliance. The second solution—from a competitor we refer to as "Vendor X"—used a similarly functioning data protection tool from the Vendor X management platform on a comparably-sized storage appliance. On both solutions, we ran three script-based malicious event scenarios that targeted data backups: encrypt all files and obfuscate file names; encrypt all files and keep original file names; and infect a Microsoft SQL Server page.
In our testing, we found that Dell PowerProtect Cyber Recovery with CyberSense provided several advantages over the Vendor X solution. To create a baseline to scan for data corruption, CyberSense only needed one full backup, while the Vendor X solution needed one full backup and 14 incremental backups. Also, the CyberSense solution was able to scan deep enough to detect infection in SQL database pages—something that the Vendor X solution couldn't do. Finally, the Cyber Recovery solution provides administrators with many options for recovering data, relying on uncompromised data from the vault for an efficient recovery process.
Our results show that for organizations that want to take a proactive approach to cyber security, Dell PowerProtect Cyber Recovery with Cyber Sense can help them manage their data and guard against destructive cyberattacks—while also helping to ensure proper database recovery and a smooth return to operations.
For more details about our data security solution comparison study, check out the executive summary, report, and infographic below.
Principled Technologies is more than a name: Those two words power all we do. Our principles are our north star, determining the way we work with you, treat our staff, and run our business. And in every area, technologies drive our business, inspire us to innovate, and remind us that new approaches are always possible.